In this blog series, our Executive Director Ben Taylor highlights a selection of cybersecurity, physical security, health or natural threat related stories relevant to the cannabis industry.
Natural Events
Response and Recovery Operations from Hurricane Ian Begin
As Hurricane Ian continues to upend the lives of millions along the southeastern United States, authorities in Florida and South Carolina have started sifting through the storm’s wreckage to assess the toll of one of the strongest, most expensive hurricanes in recent American history.Current power outage reports show Florida still has 1.2M customers without power, and the hard hit Lee County is dealing with significant water pressure issues that may require additional evacuations.
A recent MJBizDaily article on the impacts of Hurricane Ian noted the efforts of Boston-based Weedgets, which makes smoking devices and other accessories. They prepared their Miami operation by moving all inventory that was on the ground level to elevated storage. Video over social media shows how high storm surge got in Ft. Myers. Storm surge and flooding are such an important consideration when discussing hurricane planning. Businesses should consider when elevating product isn’t enough, and what are the triggers, and procedures for moving product to a safer location.
In the immediate aftermath of any natural disaster, there is the risk that cyber criminals and scammers will try to take advantage of people’s vulnerability and charity. Both CISA and the FTC have released alerts the bring attention to the potential for fraudulent activity. Cannabis operators are encouraged to educate their staff on these risks.
The below graphic from a recent MJBizDaily article shows that more than half of Florida’s 485 medical marijuana dispensaries laid within the path of Hurricane Ian.
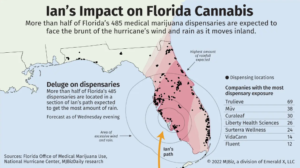
For interested businesses in Florida and other impacted regions, FEMA and CISA are holding daily private sector stakeholder calls to provide updates on the response and recover efforts. In addition, the state of Florida has requested businesses fill out a damage assessment survey which can help determine the best allocation of resources.
- Date: Daily
- Time: 3:00 pm Eastern
- Webinar Link
- Passcode: 285232
- Or One tap mobile: US: +16692545252, 1613178768# or +15512851373, 1613178768#
- Or Telephone: Dial (for higher quality, dial a number based on your current location): US: +1 669 254 5252 or +1 551 285 1373 or +1 646 828 7666 or +1 669 216 1590.
- Webinar ID:161 317 8768
- International numbers available: https://fema.zoomgov.com/u/acO9GqI1
Below are resources which may be useful to Florida businesses.
- FEMA Hurricane Incident Journal
- FloridaDisaster.Biz
- Florida Health Care Association
- Power Outage Map
- Boil Water Notices
- Road Monitoring (FL511)
- Traffic Updates
- Gas Buddy
- Florida Volunteer Opportunities
- Disaster Assistance
- SBA Disaster Loans
- Unsolicited Donations
- Locate a Shelter
- Emergency Accommodations Module
Cybersecurity
Customer Guidance for Reported Zero-day Vulnerabilities in Microsoft Exchange Server
Microsoft is investigating two reported zero-day vulnerabilities affecting Microsoft Exchange Server 2013, 2016, and 2019. The first vulnerability, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, while the second, identified as CVE-2022-41082, allows remote code execution (RCE) when PowerShell is accessible to the attacker.
At this time, Microsoft is aware of limited targeted attacks using the two vulnerabilities to get into users’ systems. In these attacks, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should be noted that authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either of the two vulnerabilities. Microsoft emphasizes that online customers do not need to take any action, and have provided mitigation steps for on premise Microsoft Exchange customers.
Additional headlines related to the Microsoft Exchange Server Zero-day Vulnerability include:
- ProxyNotShell— the story of the claimed zero day in Microsoft Exchange
- New Microsoft Exchange zero-days actively exploited in attacks
- Potential vulnerability associated with Microsoft Exchange
- Warning: New attack campaign utilized a new 0-day RCE vulnerability on Microsoft Exchange Server
Fake CISO Profiles on LinkedIn Target Fortune 500s
Someone has recently created a large number of fake LinkedIn profiles for Chief Information Security Officer (CISO) roles at some of the world’s largest corporations. Members may want to keep an eye on potential fake profiles of their leaders or fake profiles of fake employees posing as leaders. It’s not clear who’s behind this network of fake CISOs or what their intentions may be. But the fabricated LinkedIn identities are confusing search engine results for CISO roles at major companies, and they are being indexed as gospel by various downstream data-scraping sources. These profiles are popping up in Google searches as well as in respected sources like Cybercrime Magazine’s CISO 500 listing. Rich Mason, the former CISO at Fortune 500 firm Honeywell, began warning his colleagues on LinkedIn about the phony profiles earlier this week. “It’s interesting the downstream sources that repeat LinkedIn bogus content as truth,” Mason said. “This is dangerous, Apollo.io, Signalhire, and Cybersecurity Ventures.”
Mason said LinkedIn also needs a more streamlined process for allowing employers to remove phony employee accounts. He recently tried to get a phony profile removed from LinkedIn for someone who falsely claimed to have worked for his company. “I shot a note to LinkedIn and said please remove this, and they said, well, we have to contact that person and arbitrate this,” he said. “They gave the guy two weeks and he didn’t respond, so they took it down. But that doesn’t scale, and there needs to be a mechanism where an employer can contact LinkedIn and have these fake profiles taken down in less than two weeks.”
Last week we shared a resource titled “Takedown: Removing Malicious Content to Protect Your Brand”from the U.K.’s National Cyber Security Centre that can also be applicable to this issue. A robust information security program should include monitoring social platforms for potential fake accounts which could be used to phish business associates or as part of job-related scams, all of which can impact the trust of your own cannabis brand.
Hacker Shares How They Allegedly Breached Fast Company’s Site
Fast Company took its website offline after it was hacked to display stories and push out Apple News notifications containing obscene and racist comments. Yesterday the hacker shared how they allegedly breached the site with BleepingComputer. The Fast Company site today shows a statement from the company confirming they were hacked on Sunday afternoon, followed by an additional hack on Tuesday evening that allowed threat actors to push out racist notifications to mobile devices via Apple News. Details of the attack are below:
- The threat actor claims they were able to breach Fast Company after they discovered a WordPress instance used by the company for their website.
- This WordPress instance was allegedly secured using HTTP basic authentication that was bypassed. The threat actor then say they gained access to the WordPress CMS using a very easy default password that was used on “dozens” of accounts.
- Upon gaining CMS acces they say they were able to steal Auth0 tokens, Apple News API keys, and Amazon SES secrets. Using these tokens, they claim to have created administrator accounts on the CMS systems, which were used to push out the notifications to Apple News.
BleepingComputer claims they do not normally share detailed information on how a hacker gained access to a site, but as Fast Company is already mitigating the breach, they felt this information could be of benefit to other website administrators. BleepingComputer does note that these claims are solely from the alleged threat actor, and have not been verified by Fast Company.
FBI Tech Tuesday: SIM Swapping
The FBI Phoenix Field Office wants to educate the public about the dangers of Subscriber Identity Module (SIM) swapping by criminals to steal money from virtual currency accounts. How the scam works—Criminals first identify a victim who is likely to own large amounts of digital currency and obtain their phone number and mobile carrier. They then socially engineer a customer service representative to port the victim’s phone number to a SIM card and phone in their control. Once they obtain control, they will change the passwords to all accounts (email, cloud storage, and social media accounts) by using the password resets. Criminals can defeat any SMS-based or mobile two-factor authentication on any accounts with control of the victim’s phone number, and then steal the currency.
The FBI suggests these tips to protect you and your digital currency:
- Protect your personal and financial information. Don’t advertise your phone number, address, or financial assets, including ownership or investment of cryptocurrency, on social media sites.
- Take precautions giving your mobile account information to representatives over the phone. Verify the call by dialing the customer service line of your mobile carrier or place a note on your account that changes must be done in person.
- Use strong multi-factor authentication methods such as biometrics, physical security tokens, or standalone authentication applications to access online accounts.
- Do not store passwords, usernames, or other information for easy login on mobile device applications.
Honolulu Man Pleads Guilty to Sabotaging Former Employer’s Computer Network
In a guilty plea, a Hawaii man admitted to accessing his former employers internet domain management system and redirecting web and email traffic. The scheme was intended to convince his old employers to hire him back at a higher salary, to help fix their new IT problems.
While cannabis industry has often looked at insider threats in relation to theft, or how they can provide intelligence to would-be robbers (like the recent incident in Massachusetts), it is also important the industry considers how they are vulnerable to disgruntled former employees. Properly off-boarding employees is so important, and should include removing permissions and updating sensitive passwords the employee may have had access to. Security leaders need to make sure departing and former employees no longer have physical or electronic access to the organization. We have previously shared CISA’s Insider Threat Assessment Tool resource, which is a good place to start for organizations developing an insider threat plan.
Physical Security
Michigan Regulators Warn Cannabis Licensees of Increased Fraudulent Activity
Michigan regulators are warning the state’s cannabis licensees of an increased number of scams targeting their businesses. The Cannabis Regulatory Agency (CRA) issued a Sept. 30 advisory bulletin notifying businesses that fraudulent activity against licensees increased in the past several months. The fraudulent incidents have shared similar tactics:
- Licensees are contacted by phone or text message by an individual seeking to place a substantial order of marijuana or marijuana product on behalf of a license.
- The individual is knowledgeable about how to place an order and gives a license number associated with a licensed marijuana business to place the order.
- When the secure transporter arrives, the location of the delivery is not a licensed marijuana business.
According to the bulletin, “Marijuana licensees are encouraged to have their staff verify the validity of a call or text with a manager or owner before processing any orders for marijuana or marijuana product. The CRA also recommends that marijuana licensees verify the address for delivery of an order of marijuana, or marijuana product is associated with a licensed location, prior to product delivery.”
Incidents of fraudulent activity or attempted fraudulent activity that coincide with the above themes should be reported to CRA-Enforcement@michigan.gov and local law enforcement.
Check out the latest blog highlighting issues important to cannabis security!
Tweet
