In our weekly Library Card Series we highlight a selection from our resource library to help introduce the content to our industry partners.
For this post of the Library Card Series we will be reviewing the Cybersecurity & Infrastructure Security Agency’s (CISA) Ransomware Guide, which was published in September 2020 in collaboration with the Multi-State Information Sharing & Analysis Center (MS-ISAC). The guide provides an overview of ransomware covers both Ransomware Prevention and Ransomware Response. The first section talks about being prepared for a ransomware attack and gives specific examples of the kind of forms ransomware may be in. The guide details risks associated with internet facing vulnerabilities and configurations, phishing, precursor malware infections, third party entities, and managed service providers. The guide also gives tips on how to be prepared to counter a ransomware attack and what signs to be on the look out for. The second section of the article gives a checklist on what to do to have a well prepared response plan for a ransomware attack if one may occur. There are also links for more information if one would like to learn more about ransomware and strategies to prevent ransomware attacks from happening.
The recent attack on Colonial Pipeline has put ransomware in the spotlight, and multiple attacks against the healthcare industry show that these threat actors look to take advantage of organizations that are already in a vulnerable operational state. The cannabis industry could be considered similarly vulnerable as organizations deal with rapid growth and an increase in capital investment. Ransomware gangs are not afraid to extort any size corporation, as seen in the recent past with a catastrophic blow on Colonial Pipeline, and the cost of ransoms, as well as lost time are significant. Being prepared to counter cyber threats like ransomware will make the cannabis industry more resilient moving forward.
A few of the General Best Practices outlined in the Guide:
- Employ Multi-Factor Authentication for all services to the extent possible.
- Apply the principle of least privilege to all systems and services so that users only have access they need to perform their jobs.
- Leverage best practices and enable security settings in association with cloud environments, such as Microsoft Office 365.
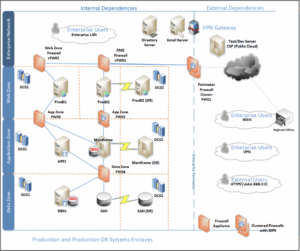
- Develop and regularly update a comprehensive network diagram that describes systems and data flows within your organization’s network (see example below)
- Employ logical or physical means of network segmentation to separate various business unit or departmental IT resources within your organization as well as to maintain separation between IT and operational technology.
- Ensure your organization has a comprehensive asset management approach.
To find more valuable resources covering a wide variety of topics, visit the resource section of our website, and check back to our blog every Tuesday for our Library Card Series where we highlight one a different resource from the library.
